Prevent Phishing
Help Keep TCU S.A.F.E.
Phishing scams are becoming increasingly sophisticated, and some have targeted TCU
community members. We want you to be informed and avoid having your information, data,
or finances compromised. Learn about our S.A.F.E. steps and follow them anytime you receive a suspicious email, text, or message.
Spot. Avoid. Flag. Evade
As scammers become more sophisticated and have access to tools like generative AI, relying on poor grammar or spelling as warning signs is no longer enough to recognize a phishing attempt. Phishing messages often disguise themselves as legitimate communication, but certain red flags may give them away. Knowing what to look for is your first line of defense.
Be on the lookout for these common warning signs in emails, texts, or messages:
- Urgent demands: Messages that pressure you to act immediately or face consequences.
- Requests for sensitive information: Asking for usernames, passwords, Okta MFA codes, or personal details.
- Account verification scams: Claiming your account needs to be verified, often providing partial information and requesting more.
- Too-good-to-be-true offers: Unsolicited job opportunities, product endorsements, prizes, or free items.
- Conversation switching: Attempting to move the conversation from email to text message.
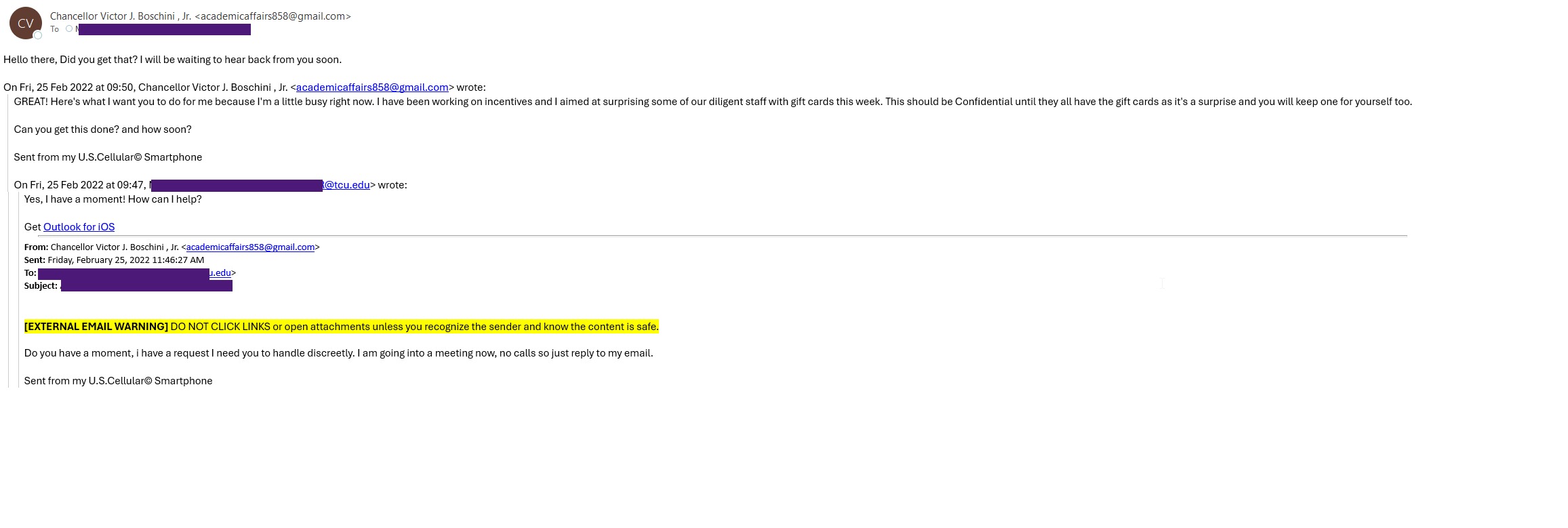
- Fake account verifications: Appearing to come from trusted accounts (such as TCU or Microsoft) and warning that your data will be deleted if you don’t respond.
- Suspicious senders: Messages from unknown groups, companies, or individuals you never signed up to hear from.
- Odd messages from known contacts: Out-of-character requests, messages from new email addresses, or instructions to use a different communication method.
Recent common scams at TCU:
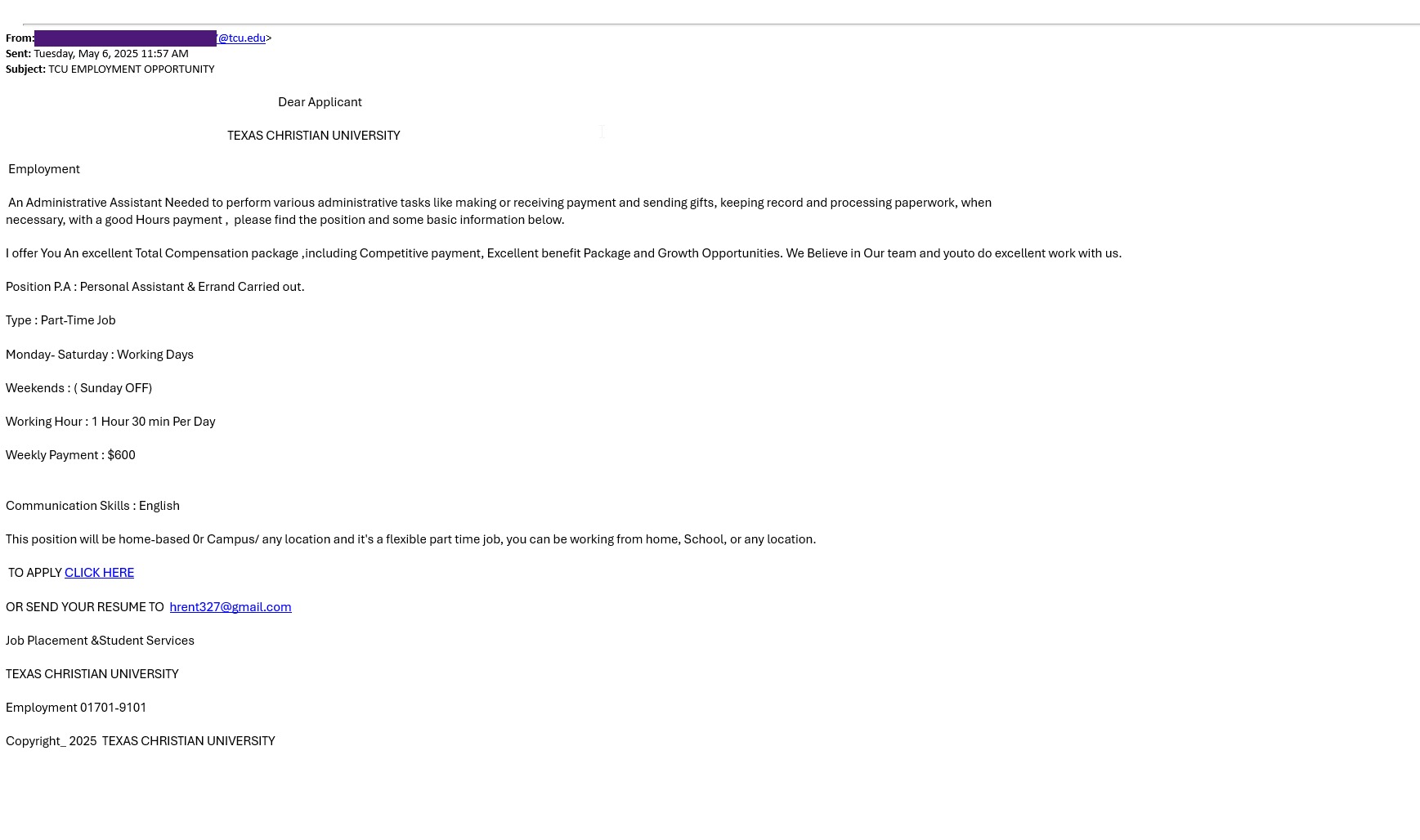
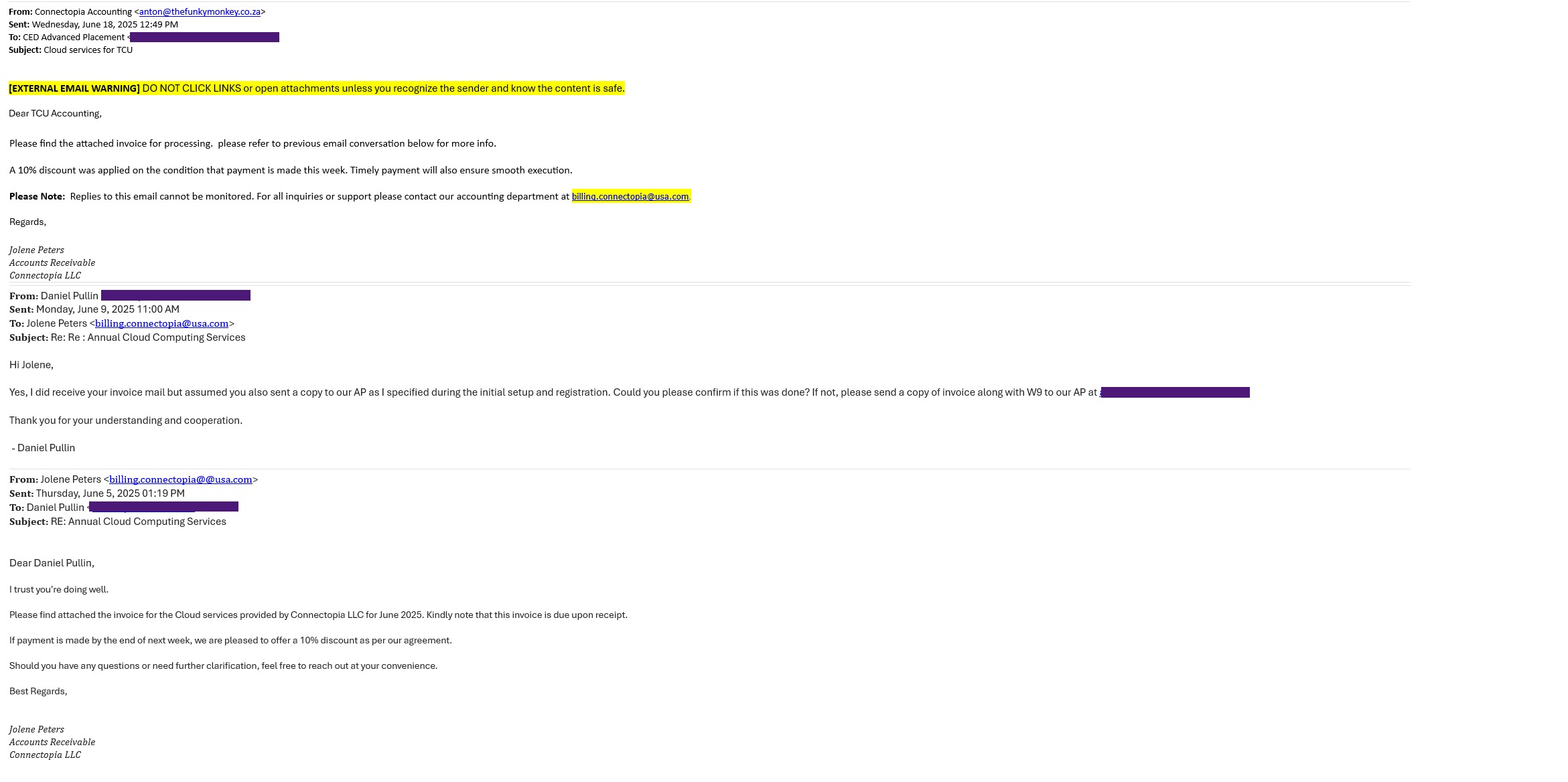
- Fake job or internship opportunities targeting students.
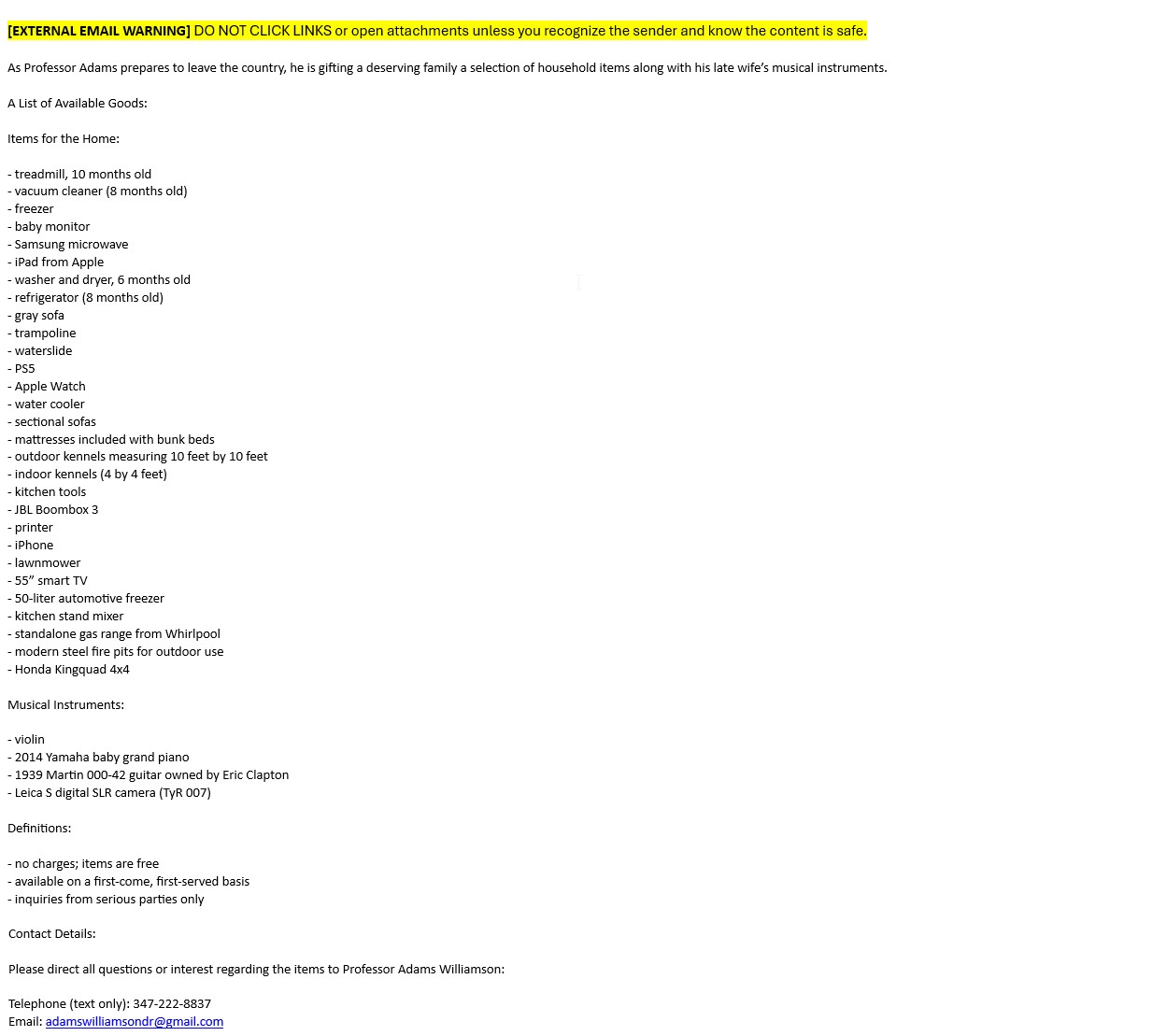
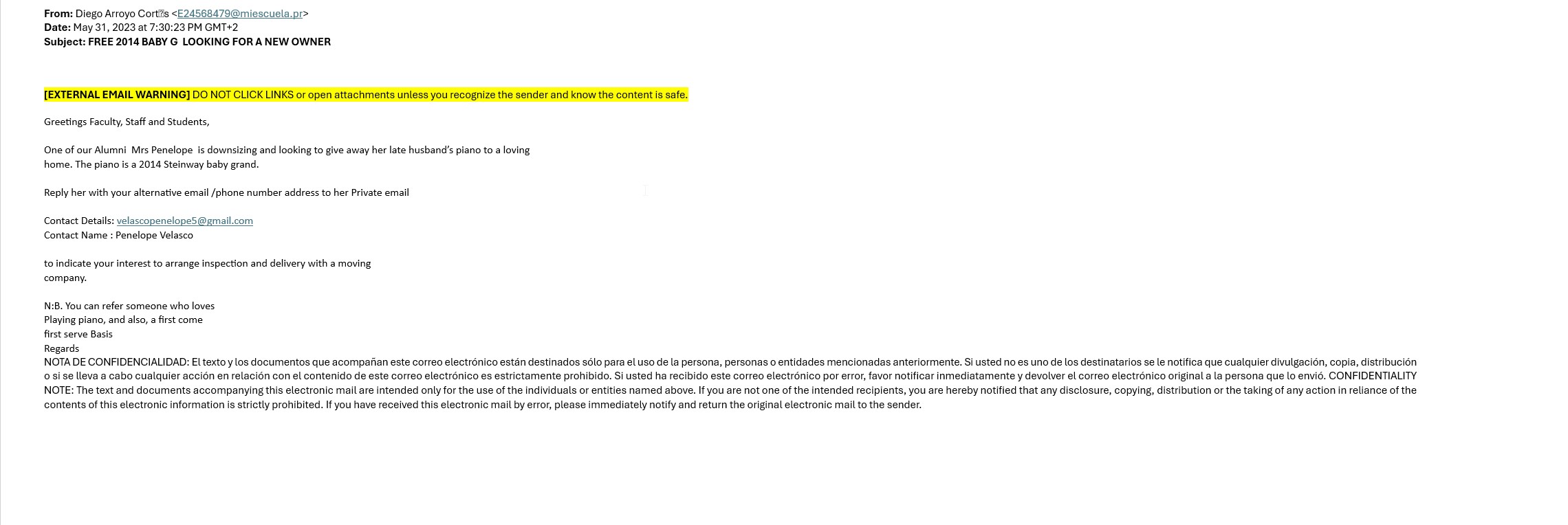
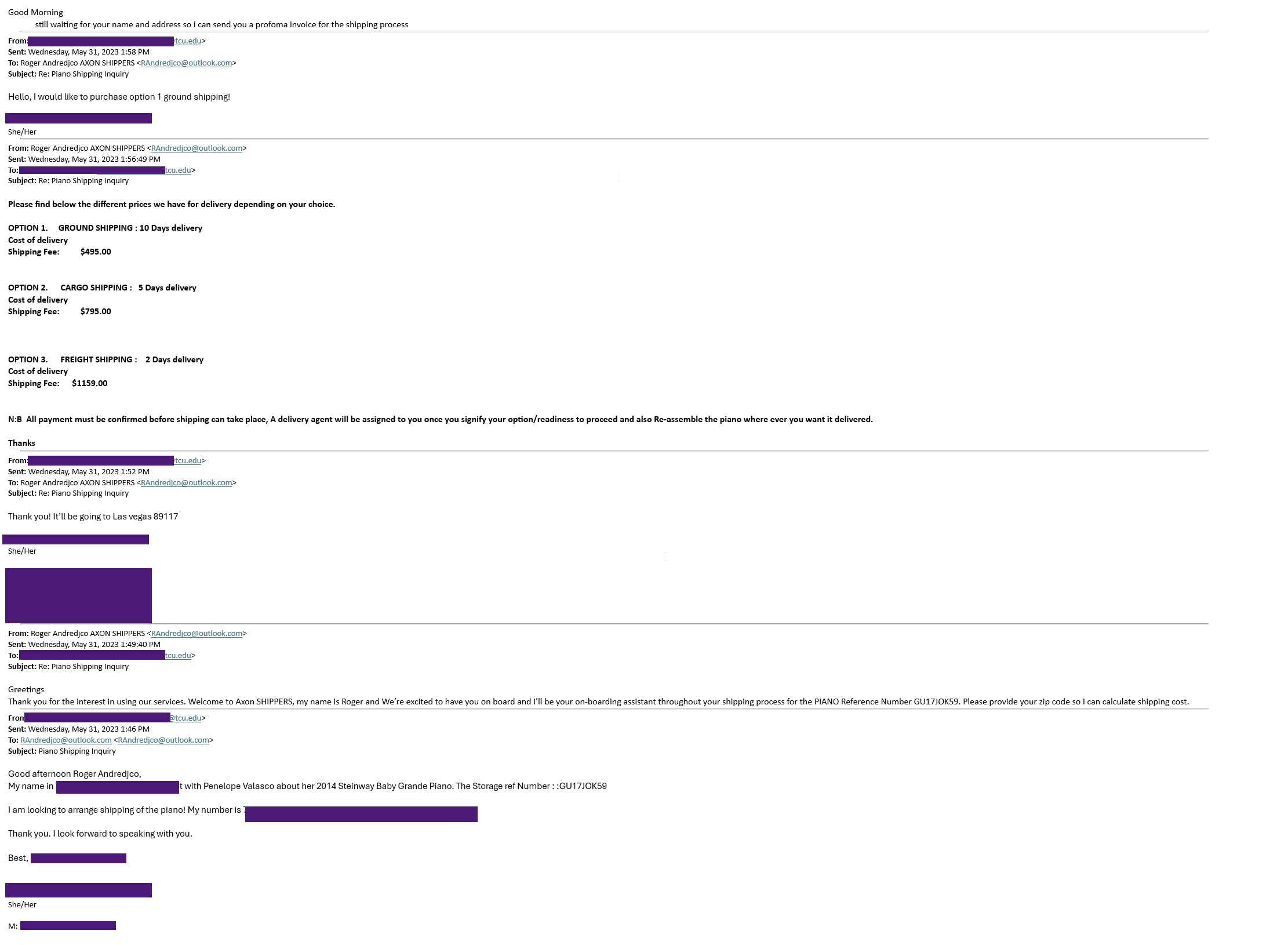
- “Free” items that require upfront shipping payments.
- Payment or subscription scams for well-known services (e.g., Netflix, PayPal).
- Gift card requests from someone posing as a supervisor, promising reimbursement.
Even if a message looks convincing, small, deliberate actions can prevent you from handing over valuable information or access. Think before you click, download, or reply.
TCU email flags external emails by highlighting a yellow bar at the top of the message, which can help alert you to senders outside of TCU, but if someone else's TCU email is compromised, scammers could send messages from a TCU email address.

Reduce your risk by always taking these precautions:
- Hover over links before clicking: Preview the real destination first.
- Check the sender’s full email address: Hover over it to see it. Don’t rely on just the display name.
- Don’t download unexpected attachments: Only open files you were expecting from a trusted source.
- Avoid entering login details on linked sites: Go to the official site directly instead.
- Skip “unsubscribe” links in suspicious emails: They may lead to a malicious site.
- Don’t enter personal information into online forms: Especially if prompted by an email.
- Avoid copying and pasting suspicious links: Even into your browser’s address bar.
- Be cautious with PDFs or other downloads: They can contain malicious code.
- Don’t install software just to open a file: Unless you know and trust the source.
Quick action can limit the damage from a phishing attack. These steps will help secure your account and reduce the risk of ongoing compromise.
If you’ve already clicked or shared information:
- Call the IT Help Desk immediately: 817-257-4357 (HELP) if you think your account has been compromised. The faster you notify IT, the better we can protect you and others.
- Change your TCU password immediately: This could help stop further access to your account.
- Monitor your accounts: Watch for suspicious activity in email, bank accounts, or other connected services.
Real Examples
In the drop downs, click the image to enlarge it.